Achievement Award
Pioneering research on an elliptic curve cryptosystem for safe IoT devices

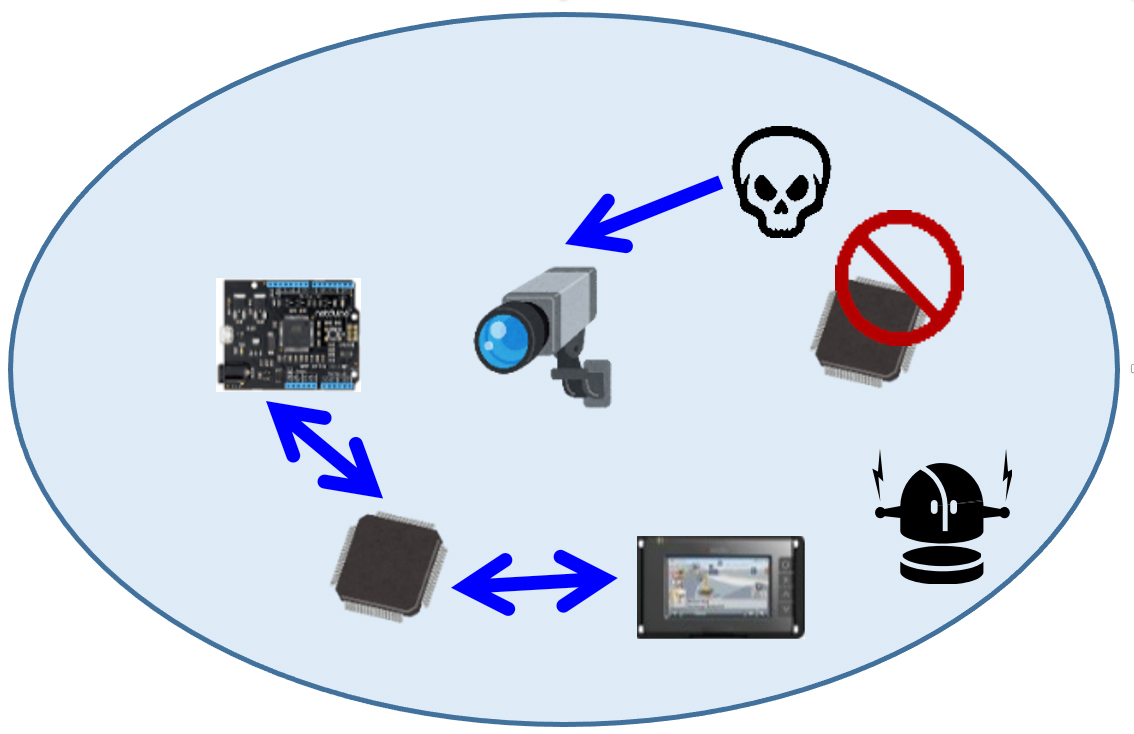
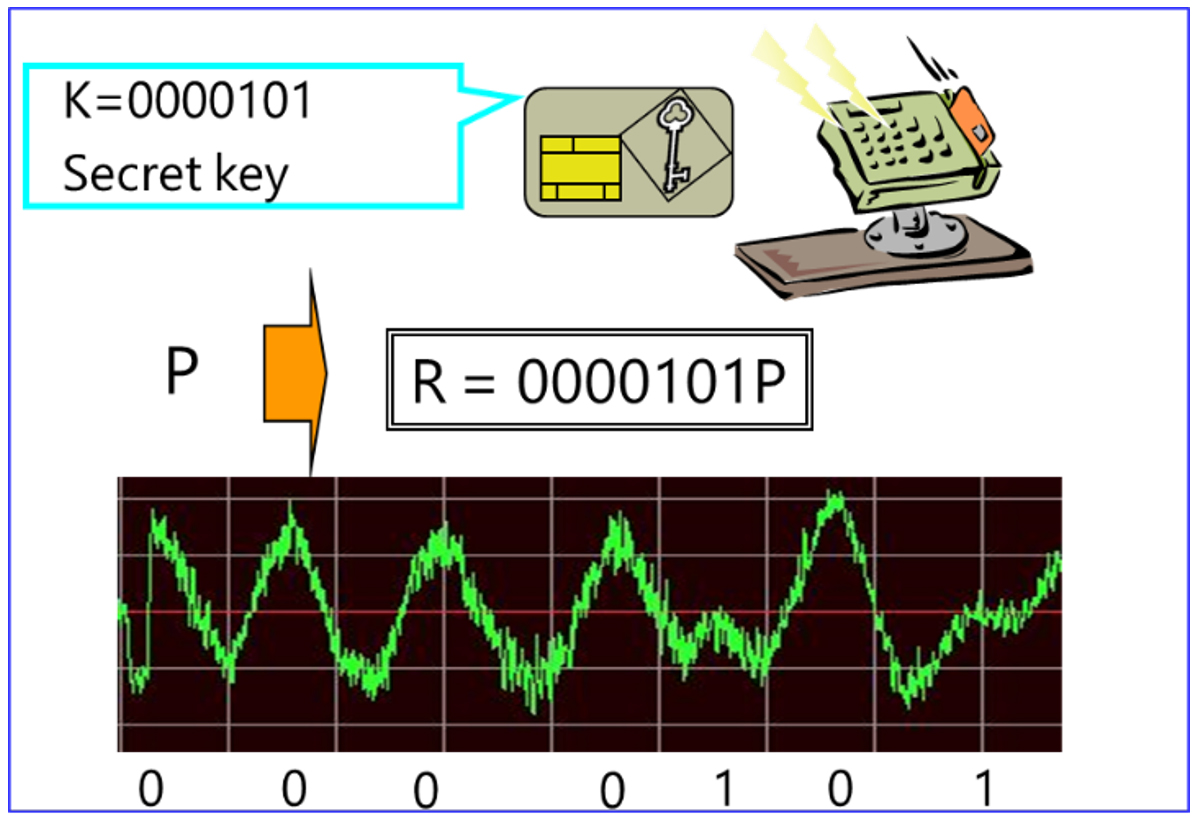
With the spread of various IoT devices, Society 5.0 is expected to be realized by the use of enormous data collected by IoT equipment. Unlike conventional network environments between fixed devices, IoT devices are often used in unmanned situations, and data from multiple devices has been leaked in various attacks, with attacked IoT devices attacking un-attacked IoT devices (Fig. 1). For this reason, equipment authentication is essential to ensure the safety of IoT devices. There are two types of cryptosystems: public key cryptosystems and a secret key cryptosystems. A secret key cryptosystem can be achieved at high speed and in a compact manner, but when using a secret key cryptosystem in IoT equipment authentication there is a risk that if one IoT device is attacked, then all IoT devices will be attacked. On the other hand, equipment authentication using a public key cryptosystem can be individually authenticated, and is desirable from the viewpoint of security. However, public key cryptosystems generally require a huge number of calculations and amount of memory compared to secret key cryptosystems, making it difficult to apply to IoT devices. Furthermore, IoT devices are often used in unmanned situations, and are also susceptible to side channel attacks using power consumption and physical information (Fig. 2).
The main contribution of this work focused on an elliptic curve cryptosystem, which is the smallest public key cryptosystem, achieving a compact elliptic curve cryptosystem that reduces the processing time and necessary memory and realizing an elliptic curve cryptosystem that is resistant to side channel attacks [2,3].
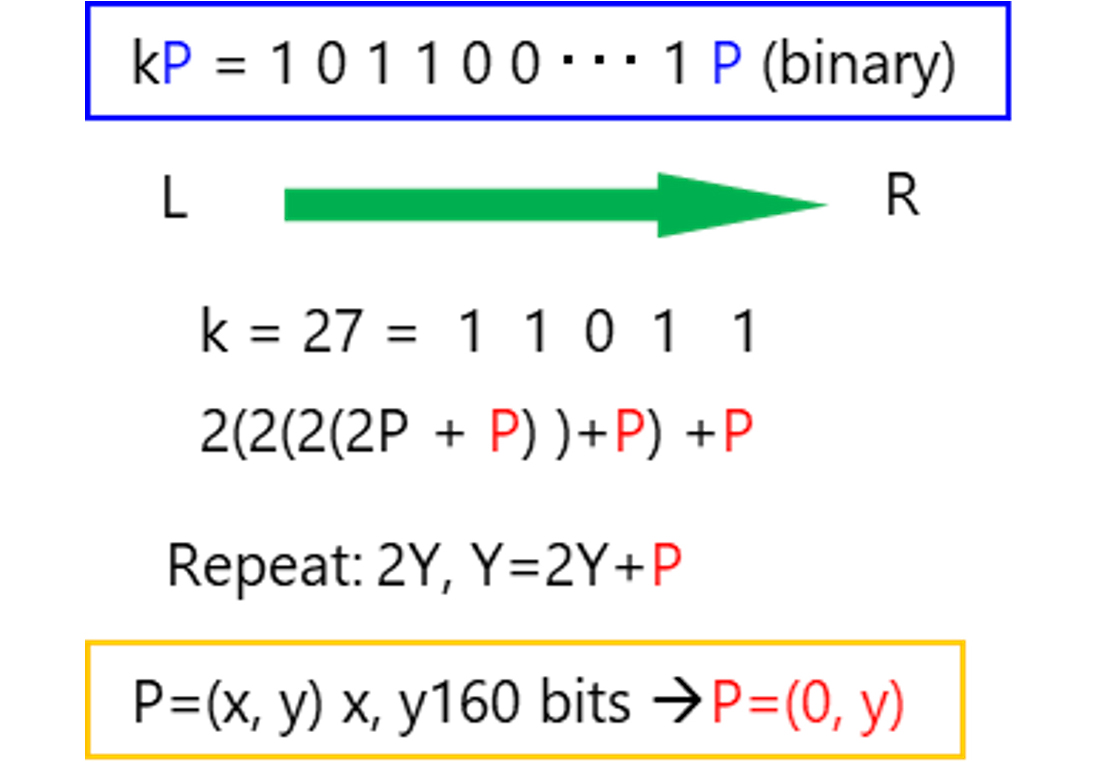
Let us first briefly explain the research of compact elliptic curve cryptosystems. The design of compact elliptic curve cryptosystems (Fig. 3) is US patented [4]. The elliptic curve cryptosystem consists of a scalar multiplication kP= P +・・・+P of P = (x, y), a curve point. Here, the size of P is generally more than 160 bits. In the scalar multiplication, the size of P is directly involved in the calculation time. In this research, an algorithm was proposed that generates a point of the elliptic curve with small X coordinates while maintaining safety. With this research, the amount of memory and number of calculations required for the retention of P enabled a compact and high-speed elliptic curve cryptosystem.
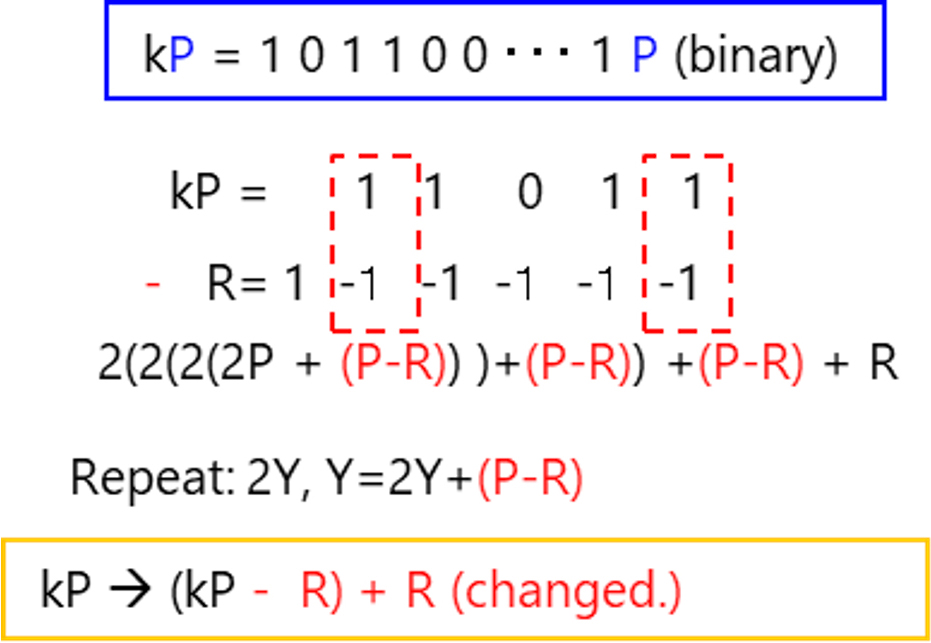
Let us briefly explain the second research of the secure elliptic curve cryptosystem. The elliptic curve cryptosystem (Fig. 4), which has side channel attack resistance, is also included in ISO/IEC international standards. The security of elliptic curve cryptosystems is based on the elliptic curve discrete lobster problem (ECDLP), which seeks a private key k for elliptic curve points P and kP. The side channel attack gets K using different power consumption in the calculation process of kP at the time of cryptosystem or signature generation depending on the value of each bit k. For this reason, it is a very threat to decipher the confidential information K independently of ECDLP mathematical difficulty. In this research, a random point R is introduced, converted the computation of KP, which is the main operation of the elliptic curve cryptosystem, to KP = (KP-R)+R, and the random point is calculated through (KP-R) and R. As a result, this invention did not depend on k and succeeded in constructing an elliptic curve cryptosystem with the same power consumption. With the present invention, a safe elliptic curve cryptosystem can be realized in the side channel attack.
In these studies, in the elliptic curve cryptosystem, the processing time and necessary memory have been reduced, and the design of an elliptic curve cipher that is resistant to side channel attacks has been realized, which has contributed greatly to the spread of secure IoT devices. Furthermore, these studies are not only for the elliptic curve cryptosystem currently used in blockchain, etc., but also an isogeny based cryptosystem, which is a post-quantum cryptosystem. The importance is very large, such as in applications to ciphers using the same copies of the same species. She also served as an editor of more than 10 international standards at ISO/IEC and contributed to the development of security technology in Japan.
As described above, the candidates have contributed to the pioneering and original researches of elliptic curve cryptosystems and international standardization activities such as the ISO/IEC editor, and these achievements are remarkable, which is appropriate for the IEICE Award.
References
- A. Miyaji, “On Secure and Fast Elliptic Curve Cryptosystems over Fp”, IEICE Trans., vol. E77-A, No.4(1994), 630-635.
- A. Miyaji, et al., “Secure Elliptic Curve Exponentiation Against RPA, ZRA, DPA, and SPA”, IEICE Trans., vol. 89-A, No.8(2006), 2207-2215.
- International Standard ISO/IEC/15946-1, Information Technology - Security Techniques - Cryptographic techniques based on elliptic curves - part 1 General, 2016.07.01 (3rd Ed.)(International standard)
- A. Miyaji et al., Method for generating and verifying electronic signatures and privacy communication using elliptic curves. US Patent 5,442,707.(Patent)